Identity and Access Management (IAM) and Authentication, Authorization, and Accounting (AAA) are two fundamental security frameworks that govern who can access what resources within a network or system. In modern cybersecurity, the AAA model is considered the foundational triad upon which the broader, more strategic IAM framework is built.
1. The Foundational Framework: AAA
AAA is a security framework that defines the necessary steps for controlling access, enforcing policies, and auditing usage of network resources (TechTarget, n.d.). The three components are sequential and interdependent.
A. Authentication (Who are you?)
This is the process of verifying a user’s claimed identity. It answers the question, “Are you who you say you are?”
- Techniques:
- Password-Based: The simplest form (something you know).
- Multi-Factor Authentication (MFA): Requires two or more verification methods from different categories, significantly enhancing security.
- Biometrics: Using unique physical attributes like fingerprints or facial recognition (something you are).
- Passwordless: Using technologies like Passkeys (FIDO2/WebAuthn) to eliminate reliance on traditional passwords.
B. Authorization (What can you do?)
This is the process of granting or denying a confirmed user access to specific resources or functions. It answers the question, “What are you allowed to do?”
- Techniques:
- Role-Based Access Control (RBAC): Permissions are grouped into specific roles (e.g., “Developer,” “HR Manager”), and users are assigned those roles.
- Attribute-Based Access Control (ABAC): Access decisions are made dynamically based on a set of attributes (e.g., user’s location, time of day, or resource sensitivity). This offers more granular control than RBAC.
- Principle of Least Privilege (PoLP): A core tenet ensuring that users are granted only the minimum access necessary to perform their job duties.
C. Accounting (What did you do?)
This is the process of tracking, monitoring, and recording all user activity while they are logged into the system. It answers the question, “When, for how long, and what exactly did you access?”
- Techniques:
- Logging and Auditing: Collecting detailed logs of login/logout times, services used, and configuration changes.
- Compliance: Providing the necessary trail data for regulatory audits (e.g., HIPAA, SOX, GDPR).
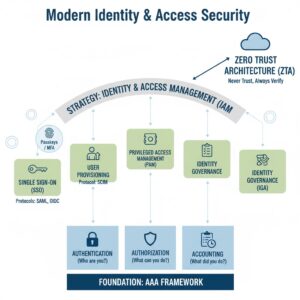
2. The Comprehensive Strategy: IAM
IAM is the overarching framework of business processes, policies, and technologies that manage digital identities and control how those identities can access enterprise resources. IAM leverages the AAA principles to create a unified system.
Key IAM Techniques and Technologies
IAM focuses on the entire lifecycle of an identity, from creation to termination.
- Single Sign-On (SSO): A user authenticates once with an Identity Provider (IdP) (e.g., Okta, Entra ID) and gains access to multiple independent applications (Service Providers).
- Protocols: SAML (Security Assertion Markup Language) and OpenID Connect (OIDC) (built on OAuth 2.0) are the standards used for this communication (Okta, n.d.-a).
- User Provisioning and Deprovisioning:Automated creation, modification, and deletion of user accounts across all applications. This is critical for security when an employee is offboarded.
- Protocol: SCIM (System for Cross-domain Identity Management) is the app-level REST protocol that standardizes this process (Okta, n.d.-b).
- Privileged Access Management (PAM): Dedicated security for accounts with elevated permissions (e.g., System Administrators, Root accounts). PAM refers to the strategy and technology to control, monitor, secure, and audit these high-value identities and activities (CyberArk, n.d.).
- Identity Governance and Administration (IGA): Processes that ensure access rights are appropriate and reviewed regularly, often including access certification/reviews to find and remove excessive or “stale” permissions.
3. The Future of IAM and AAA
The industry is rapidly shifting toward more dynamic and risk-aware security models:
- Zero Trust Architecture (ZTA): The core principle is “never trust, always verify.” Every access request, regardless of where it originates, must be continuously validated using context, behavior, and policy. IAM is the control plane for ZTA (NIST, 2020).
- Adaptive Authentication: Using machine learning to analyze user behavior (time of day, location, device) to calculate a risk score for every login attempt, allowing for Adaptive Authentication—if the risk is high, MFA is triggered; if low, access is granted seamlessly.
📚 References
Use these entries for your “References” or “Sources” section.
- CyberArk. (n.d.). What is Privileged Access Management (PAM)? Retrieved November 19, 2025, from [Insert the specific CyberArk URL for PAM definition].
- National Institute of Standards and Technology (NIST). (2020). Zero Trust Architecture (NIST SP 800-207). U.S. Department of Commerce. [Insert the direct link to the NIST SP 800-207 PDF or summary page].
- Okta. (n.d.-a). OpenID Connect & OAuth 2.0. Okta Developer. Retrieved November 19, 2025, from [Insert the specific Okta Developer URL for OIDC/OAuth 2.0 overview].
- Okta. (n.d.-b). SCIM 2.0 Protocol Reference. Okta Developer. Retrieved November 19, 2025, from [Insert the specific Okta Developer URL for SCIM 2.0 protocol].
- TechTarget. (n.d.). What is AAA (authentication, authorization and accounting)? Retrieved November 19, 2025, from [Insert the specific TechTarget URL for AAA definition].



