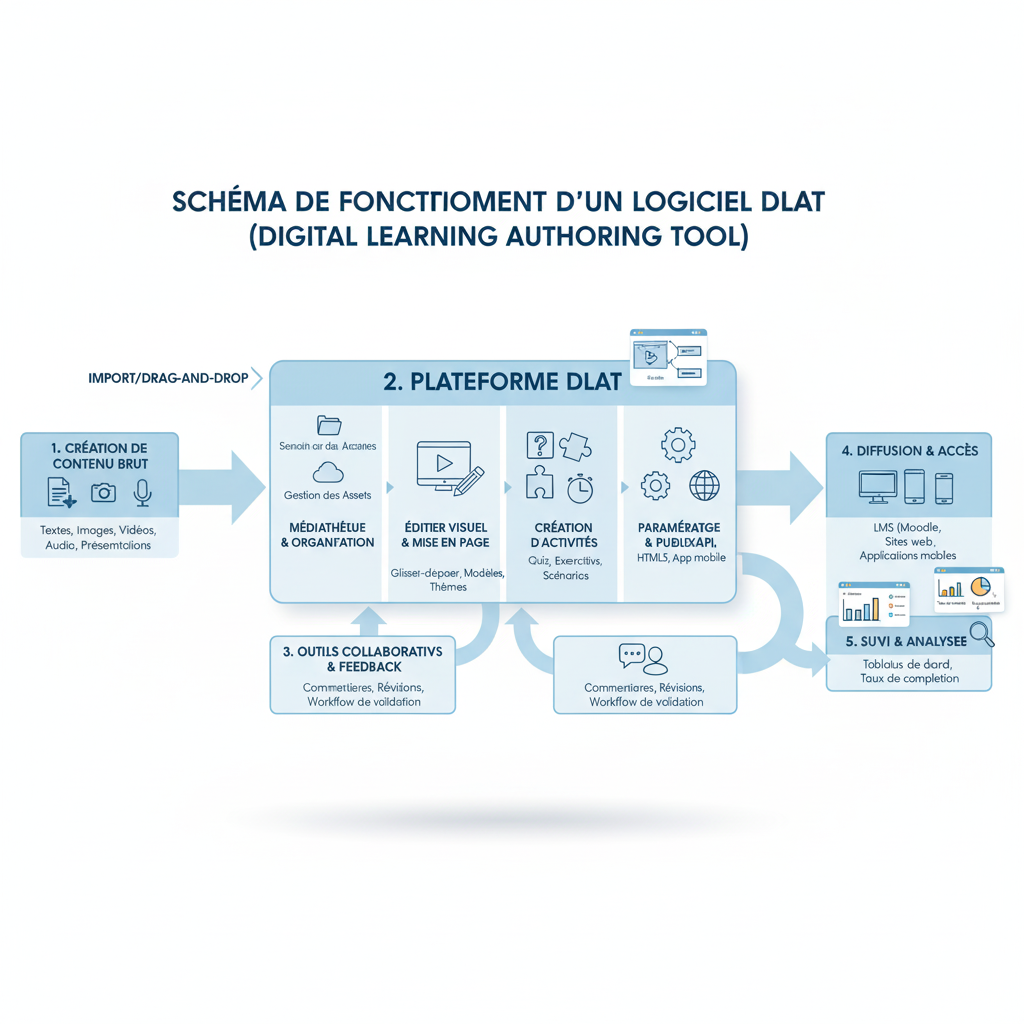
Whar are DLPs?
November 15, 2025
0 Comments
Explore More
The Security Triad: Confidentiality, Integrity, and Availability

In the realm of information security, the Security Triad, often referred to as the CIA Triad, is a foundational model designed to guide policies and practices for information security. It
OSINT: How Open Source Intelligence is Revolutionizing Cybersecurity and Investigation

The term OSINT (Open Source Intelligence) is on everyone’s lips, from cybersecurity analysts to investigative journalists. Far from sophisticated espionage, OSINT is the art of transforming publicly accessible information into
Protecting Personal Data: PII and SPII Regulations in Europe and France

In today’s digital age, the protection of personal data is paramount. With the increasing volume of information collected and processed, robust legal frameworks are essential to safeguard individuals’ privacy. Europe,